By Dr. Klaus Gheri, VP & GM Network Security at Barracuda Networks
Attacks aimed at identity misuse and account takeover have become increasingly sophisticated over time, as they are an easy gateway for cybercriminals to enter a company’s network in order to tap into sensitive data or carry out further attacks. In the first half of 2023, Barracuda collected nearly one trillion IT events, and among them, the most frequently detected high-risk incidents requiring immediate defensive action were related to some kind of identity misuse.
However, with the help of AI-based account profiling, these attacks can be detected and blocked. This is because in a work context, everyone has a distinct digital profile in terms of how, where and when they work. If an IT event falls outside this pattern, the system sounds the alarm. Even when attacks are so subtle and sophisticated that human expertise is required to investigate, AI-based detection ensures that an experienced SOC analyst confirms the malicious intent of the attack.
The most frequently detected high-risk attacks: results in detail
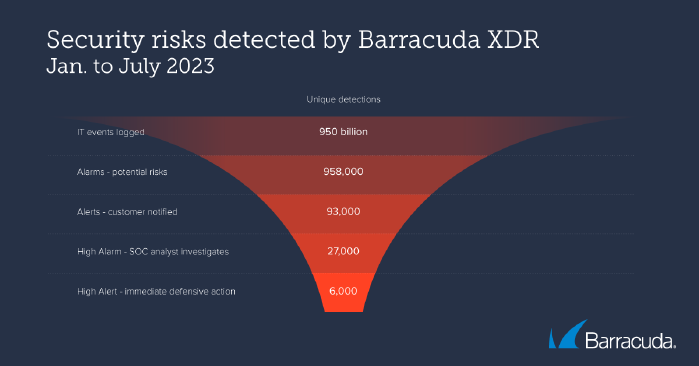
Between January and July 2023, Barracuda’s Managed XDR platform collected 950 billion IT events from its customer organisations’ integrated network, cloud, email, endpoint and server security tools. These nearly one trillion events include everything from logins (successful and unsuccessful), network connections and traffic flows to email messages and attachments, files created and saved, application and device processes, configuration and registry changes, and specific security alerts.
0.1 per cent of these events (985,000) were classified as alerts, activities that could be malicious and require further investigation. Of these, 1 in 10 (9.7 per cent) were reported to the client for review, while a further 2.7 per cent were classified as high risk and referred to a SOC analyst for more detailed analysis. 6,000 attacks required immediate defensive action to contain and neutralise the threat.
The three most common high-risk attacks detected and investigated by SOC analysts in the first six months of 2023 were:
1. login event “Impossible Journey”.
These events occur when detection shows that a user is attempting to log into a cloud account from two geographically disparate locations in quick succession – where the distance between the two locations is impossible to travel in the time between logins. While this may mean that the user is using a VPN for one of the sessions, it is often an indication that an attacker has gained access to the user account. Therefore, “impossible trip” logins should always be investigated. The Barracuda XDR “Impossible Travel” detection for Microsoft 365 accounts detected and blocked hundreds of attempted BEC (Business Email Compromise) attacks between January and July 2023 alone.
A real-world example: In one incident investigated by the Barracuda SOC team, a user logged into his Microsoft 365 account from California and just 13 minutes later from Virginia. The IP address used to log in from Virginia was not associated with a known VPN address, and the user did not normally log in from that location. The SOC team notified the client company, who confirmed that this was an unauthorised login, immediately reset the passwords and logged the user out of all active accounts.
2. anomaly detections
AI-based account profiling can also be used to identify unusual or unexpected activity in a user’s account. This may include infrequent or unique logon times, unusual file access patterns, or excessive account creation for a single user or organisation. Deviations from a user’s usual account behaviour pattern should always be investigated to clarify the cause of the anomaly, as it can be indicative of a variety of issues, including malware infections, phishing attacks and insider threats.
3. communication with known malicious artefacts.
These detections identify communication with suspicious or known malicious IP addresses, domains or files. This may be a sign of a malware infection or phishing attack. Upon detection of communication with a known malicious or suspicious artefact, the computer should be immediately quarantined and scanned for infection.
AI in the hands of attackers
While the above shows how AI can significantly improve security, it can also be used by attackers for malicious purposes. For example, cybercriminals can use generative AI language tools to create highly convincing emails that closely resemble the style of a legitimate business, making it much harder for individuals to tell if an email is legitimate or if it is a phishing, account takeover or BEC attack.
AI tools are also likely to be used by attackers to automate and dynamically emulate malicious software behaviours, making their attacks more effective and harder to detect. For example, AI-powered command-line tools can quickly adapt to changes in an attack target’s defences, detect vulnerabilities, or even learn from previous failed attempts to optimise subsequent attacks. A first example of such a tool is “WormGPT”, which is already being promoted in an underground forum and can be used by threat actors to automate the creation of malicious scripts and commands and dynamically adapt them to each specific target.
Security for a rapidly evolving threat landscape
As AI continues to advance, organisations need to be aware of the potential risks and take steps to mitigate them. This includes robust authentication measures, such as at least multifactor authentication, but ideally zero-trust approaches, as well as ongoing employee training, especially with regard to phishing attacks.
IT security teams and their external security vendors should try to stay informed about the latest AI-based threats and adapt their security measures. However, it is equally important to remember the basics: systems and software should always be up to date and professionals should have a complete overview of the IT environment.
In addition, the use of integrated security services and platforms for managed support, XDR and SOC-as-a-Service can help companies and their internal security team monitor, detect and respond to cyber threats around the clock to defend against the increasingly complex threat landscape.