ESET study confirms trend towards “EDR” (Endpoint Detection and Response) worldwide
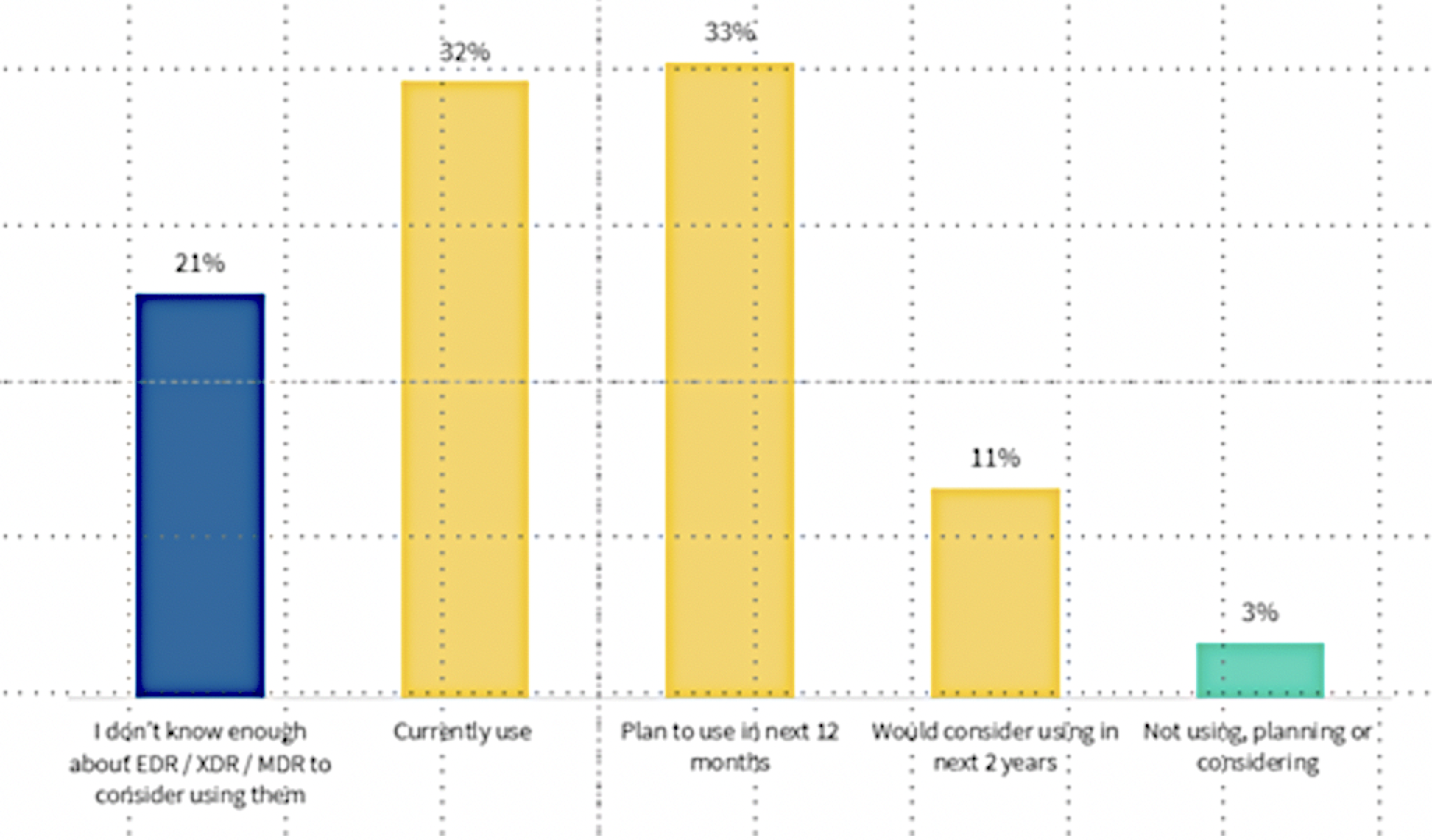
Fend off sophisticated hacker attacks, find internal security holes and be prepared for zero-day exploits: The specifications demanded much more from IT security teams than they were able to do with malware protection, firewalls and a few other tools. However, a current international study by the IT security manufacturer ESET shows that more and more companies have recognised the security signs of the times. They are already increasingly investing in modern endpoint detection and response solutions – EDR for short. 31 percent of the German companies surveyed stated that they already use EDR solutions. Another 32 percent plan to operate them in the next twelve months and ten out of a hundred in the next two years. This puts Germany overall on par with the EMEA region, but well ahead of North America.
“Successful cyber attacks on companies rarely happen at the drop of a hat, but are the result of longer and, above all, more elaborate preparations on the part of the hackers. Especially when advanced persistent threats and zero-day exploits come into play, however, classic security products reach their limits,” says Michael Schröder, Manager of Security Business Strategy at ESET Germany. “While these threats can rarely be detected directly, such as malware, they can be detected immediately as an anomaly in the network. Endpoint detection and response tools are supporting the IT security teams of more and more SMEs.”
Global trend towards EDR clearly evident – also among SMEs
ESET’s international study clearly shows that almost two-thirds of the 1212 companies surveyed are already using EDR or intend to do so in the next twelve months. This is all the more remarkable as endpoint detection and response solutions have so far tended to be found in large companies with the corresponding resources.
In the ESET survey, however, classic SMEs with between 25 and 500 employees had their say. From this, it can be deduced that EDR solutions have long since reached SMEs. The security experts attribute this to the fact that modern endpoint detection and response solutions are easier to operate and many activities can be automated. This saves financial and personnel resources. In addition, more and more managed (security) service providers are jumping on the bandwagon and offering EDR as a service. But manufacturers like ESET also offer their own services in addition to EDR solutions, which customers can book directly.
Europe is ahead in a short-term, worldwide comparison
The topic of EDR seems to have become more popular or faster in everyday IT life in Europe than in North America. In EMEA, 67 per cent of respondents said they were already using EDR or would implement it in the next 12 months. In the NORAM countries, the figure is only 58 per cent. Only in one European country (Italy, 54 per cent) is EDR slightly less common. The leaders are the United Kingdom and Denmark (76 %), Poland (74 %) and Spain (70 %). Germany ranks in the lower midfield with 63 percent.
Need to catch up in terms of knowledge about EDR
Even though the above-mentioned figures paint a positive picture, the topic of endpoint detection and response is still far from being on everyone’s mind. When asked whether they were familiar with EDR, 31 percent of respondents (Canada) answered that their knowledge was not sufficient to make a decision in favour of such solutions. In EMEA, this was stated by one in five, in North America even by one in four. There were major differences in the EMEA countries: While Denmark (13 %), Poland (15 %) and the Czech Republic (16 %) shone with comparatively low values, Sweden (28 %) and Italy (26 %) have some catching up to do. Germany is again in the middle of the pack with 22 %.
Background: Why Endpoint Detection and Response is so successful
Endpoint detection and response solutions significantly increase the level of protection for companies and provide IT security managers with a comprehensive internal view of their network. But what does detection and response actually mean in practice? On the one hand, it is intended to protect the endpoint (“detection”), where most hacker activities take place. This is where the majority of data worthy of protection is located, or where passwords or bank data, for example, are entered on the device. On the other hand, “Response” describes that it is possible to react immediately to anomalies.
All activities within the IT infrastructure (user, file, process, registry, storage and network processes) can be monitored and evaluated in real time thanks to EDR. If necessary, the IT manager can immediately take manual action or automatic, previously defined behaviours can intervene. Only in this way can the first traces of hackers be identified, employee misconduct determined and security deficiencies pinpointed. Or find the gateways that were too wide open during a successful hacker attack on one’s own network.
The evaluation of all endpoint data in a network allows conclusions to be drawn about the validity of individual processes. A precise recording of everyday processes such as the copying of files, user accesses to certain areas in the network, but also user logins and logouts, allows malicious activities to be filtered out with the appropriate evaluation.
In addition, endpoint and response solutions offer another important application: with their help, forensic investigations can be carried out after a cyberattack. Similar to a murder case in well-known crime novels, as much information as possible is collected and alibis, in these cases the proper working methods, are checked. Administrators can then reliably identify how the attack took place, which vulnerabilities were specifically exploited and what changes were made to the network.
ESET will be exhibiting at the IT security trade fair it-sa in Nuremberg (25 to 27 October 2022). At stand 7-530, interested parties can obtain first-hand information on the topics of endpoint detection and response, managed detection and response (MDR) and extended detection and response (XDR). https://www.eset.de/itsa