With an exploding number of cyber attacks in the past two years, it is more important than ever for companies to protect and continuously adapt their IT infrastructures. To achieve this, pentests should be conducted regularly.
Since the pandemic, hacker attacks on companies have increased significantly. The approaches are more creative and diverse. With cybercrime-as-a-service, even laymen can hack entire systems. In its most recently published status report for 2021, the German Federal Office for Information Security (BSI) records an increase to 394,000 new malware variants – per day. The trend is rising. For the German economy, cyber attacks mean losses in the billions. An average of 223 billion euros – that’s what a Bitkom study found out.
Check cyber security with pentesting
For protection, cyber security measures in companies should be continuously checked and optimised. This is possible with penetration testing, or pentesting for short. The aim of this procedure is to crack the security system without causing actual damage to the company. For this purpose, current hacker methods are used to check whether there are weak points in the cyber security and where they are located. Based on this knowledge, the security measures can be optimised.
The fact that cyber security can withstand current hacker attacks is generally important. However, the security level becomes even more important when companies process sensitive data. If organisations count as critical infrastructures, then they are legally obliged to keep their security measures up to date and to check them regularly. Those who want to insure themselves against cyber attacks – for example, through cyber insurance – can use pentests to prove that the company meets the requirements.
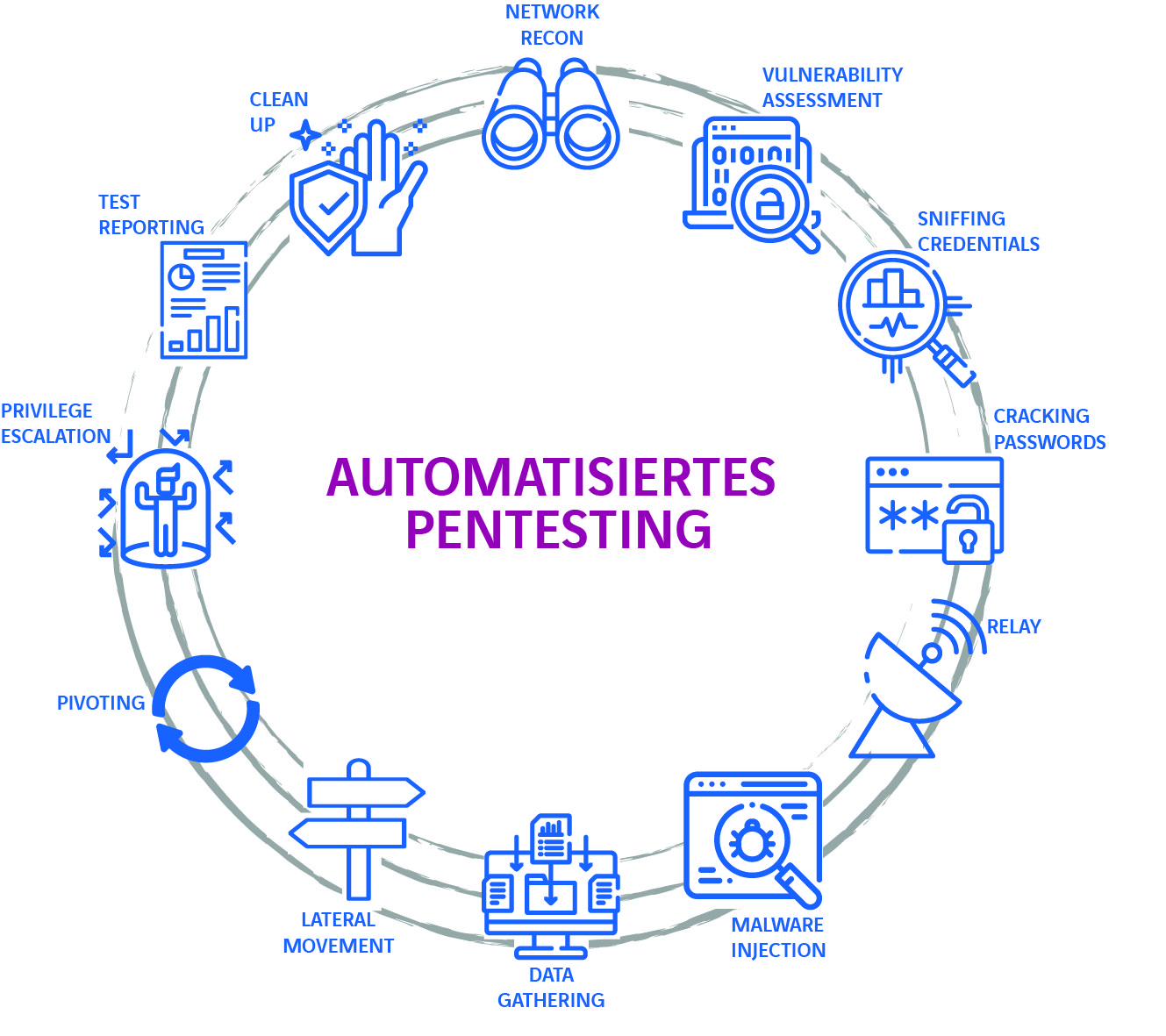
Which is better: automated or manual pentesting?
A pentest can be carried out in two ways: automated or manual. Automated pentests are becoming more and more widespread because they save time and money compared to manual testing. Automated pentesting is also suitable for large and complex IT environments. In addition, the results of automated tests can be reproduced regardless of which staff members are carrying them out, which means that test results can be compared and standardised, consistent quality can be guaranteed. In this way, uniform testing of security measures is possible at all locations.
Due to the high costs and time involved, manual pentesting is now only worthwhile in selected scenarios – for example, to check special cases or for whiteboxing tests. According to a study by the cyber security provider Pentera, most companies currently perform pentests only once a year. This is because automated pentesting has not been on the market for long. Companies should urgently take advantage of the offer to carry out pentesting several times a year for a similar amount of money and time and to obtain comparable results. After all, a one-time test is only a snapshot, and both the attack techniques of hackers and the IT environments develop in a highly dynamic manner. This requires a continuous adaptation of cyber security measures.
External and internal pentests
Basically, a distinction is made between external and internal pentests. The former checks the vulnerability from the outside: company networks, web presences as well as systems. If a hacker has already penetrated the network, the internal pentest is used. Here it is determined what damage attackers:inside can cause after they have penetrated – which data is vulnerable or can even the entire system be taken over. This means that they can be given a special weighting. Because hackers often get into the system through human actions – phishing emails or deep fakes are popular methods to deceive employees. Even an infected USB stick can open doors for criminals.
The three approaches to pentesting
There are three different approaches to pentesting. The approaches to pentesting are called black box, grey box and white box. The fact that the whitebox approach is most suitable for the manual process is due to the fact that it is an audit. Here, the complete system documentation is exposed. If it is only a question of checking compliance with regulations, this approach is sufficient. The other two test variants can be carried out automatically.
The black box approach is the counterpart to pentesting according to the white box methodology and presents the testers with a real challenge. All information must be collected by the testers themselves. This includes the type of operating system, access data and the IT infrastructure.
The greybox variant – also known as the what-if test – is a grey area in the truest sense of the word. This is because some information, such as employee login data, is already known. This allows scenarios to be simulated in a targeted manner. The most sensible approach is a combination of black box and grey box, starting with the former. In the case of very well shielded systems, one finally switches to the greybox approach.
Pentesting as a managed service
In principle, it is no problem to carry out automated pentesting on your own. No additional staff is needed in the IT department and the software is quickly installed and set up. However, expert knowledge is required to evaluate the results. Therefore, it is advisable to work with a Managed Security Service Provider (MSSP) such as Axians. After all, identifying the security gaps is only the preliminary work. In the follow-up, companies must be able to prioritise the vulnerabilities and take appropriate measures to close the gaps. A specialised external partner not only prepares reports and evaluates the results, but also provides the software and carries out assessments as agreed.
Regular pentesting improves cyber security
The mere fact that cybercriminals’ methods are evolving at a rapid pace and becoming ever more creative should be incentive enough for companies to regularly monitor their security measures. Automated pentests are a cost-effective way to check cyber security several times a year. Those who want to save themselves the workload and would like advice on the results and further procedures should work with a managed security service provider.

The author: Dennis Fröhlich, IT Security Consultant at Axians IT Security